Challenge Questions
Record any observed symptoms of infection from initial detonation. What are the main symptoms of a WannaCry infection?
-
New files are observed on the desktop which includes @WanaDecryptor@.exe, @Please_Read_Me@.txt, available_packages.txt.WNCRY, @WanaDecryptor@.bmp.
-
Also, I had a helloworld.txt file I can see its now helloworld.txt.WNCRY. Its content unviewable.
-
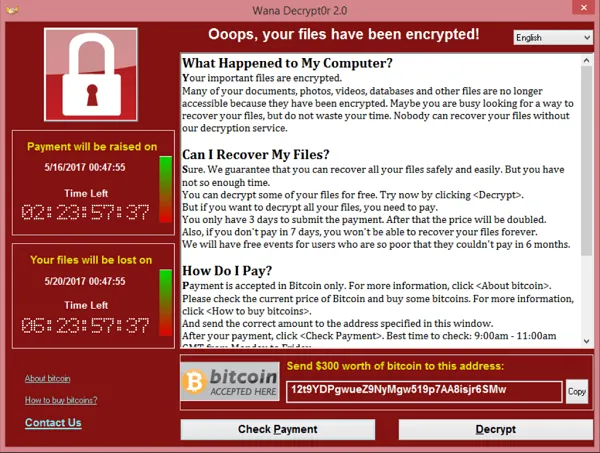
Pop up window stating file have been encrypted
- Stating “What happened to My Computer”
- How to Recover Files.
- How to Pay
- Contact info.
- Deadline for payment and payment increase.
- Bitcoin address to send money to.
Use FLOSS and extract the strings from the main WannaCry binary. Are there any strings of interest?
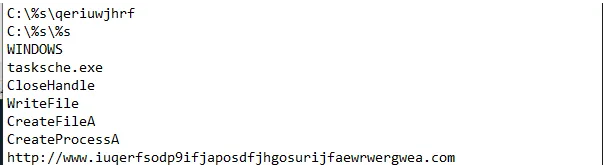
- Using Floss to exract string from malware
- Some interesting findings which includes a URL http://www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com that might be related to the malware.
- potentially folder (\qeriuwjhrf) with the path provided later on with %s. Along with CreateFileA api.
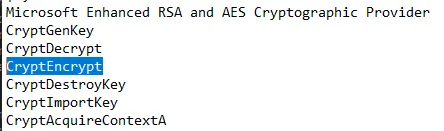
- Cryptography APIs getting called which includes:
- CryptEncrypt: for encrypting data
- CryptGenKey: for generating the public/private key pair.
Inspect the import address table for the main WannaCry binary. Are there any notable API imports?
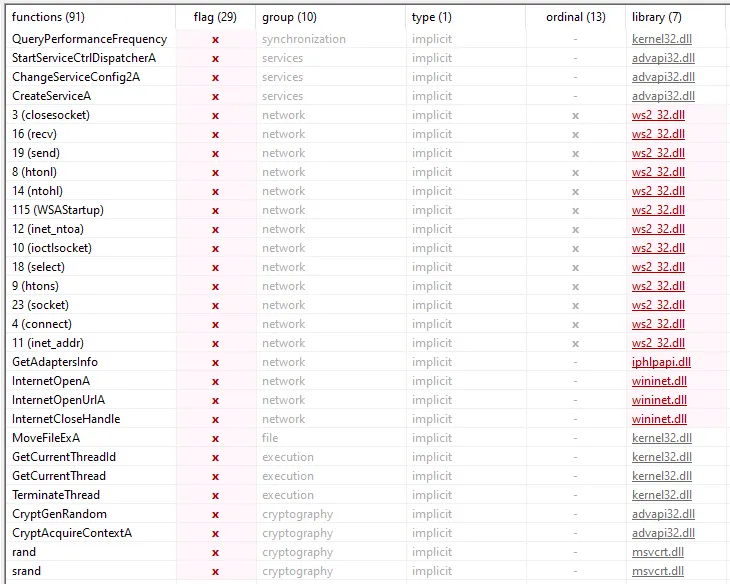
- Looking at the API imports using Peview
- InternetOpenA, InternetOpenUrlA, InternetCloseHandle: Those Api usually used my malware to connect to internet and download malicious files.
- CreateServiceA: usually used by malware for persistence by creating a service object to service control manager.
- CryptGenRandom: more api calls cryptographically related.
What conditions are necessary to get this sample to detonate?
Having inetsim running to simulate internet services didn’t cause the malware to detonate but not running it caused the malware to detonate. Maybe malware detects inetsim?
Network Indicators: Identify the network indicators of this malware
- Looking at wireshark:
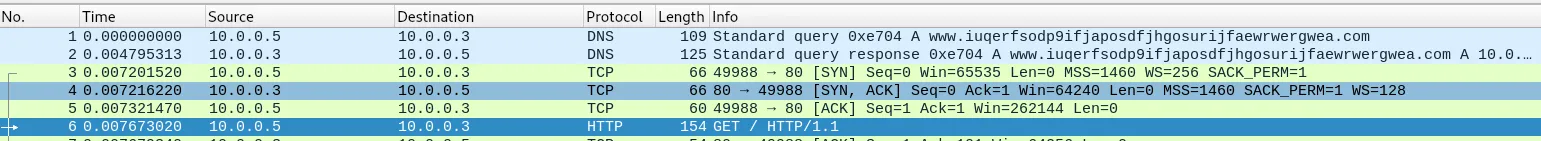
- We can see www. iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea .com the domain seen earlier in strings through DNS query and HTTP reqeust
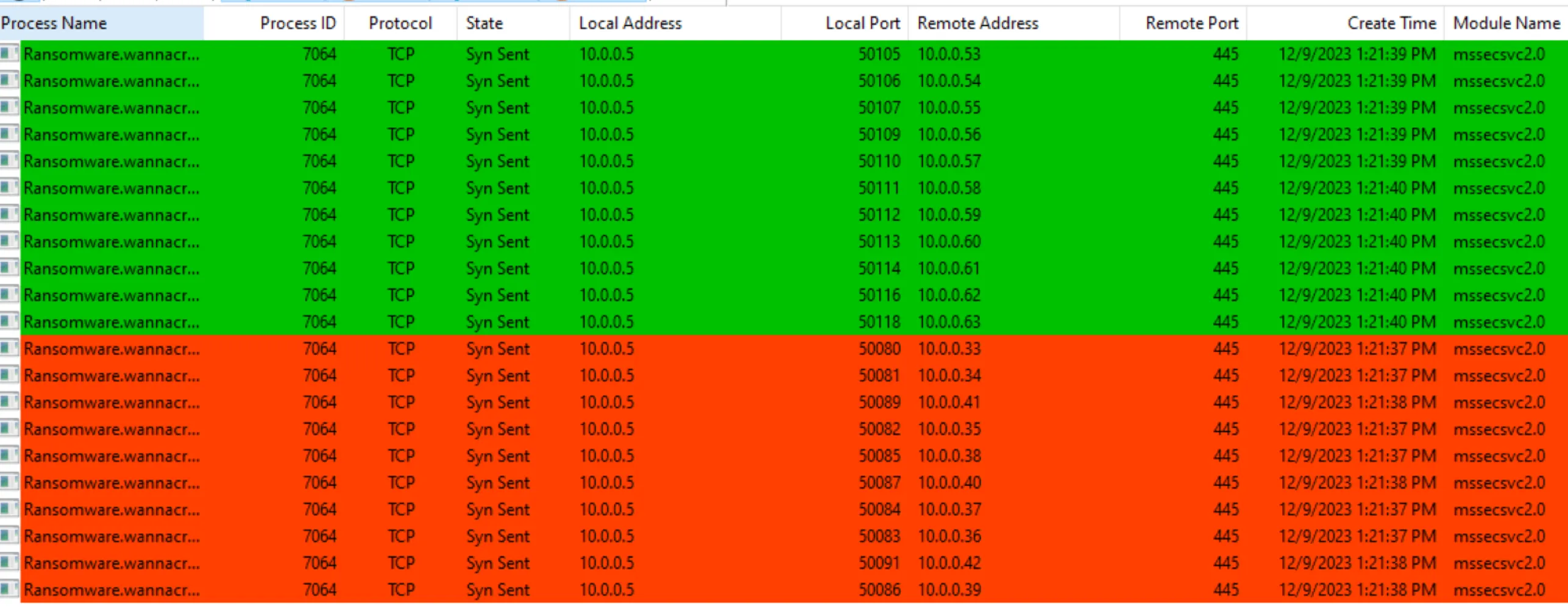
- lots of requests to every Ip address in the subnet indicating its a worm trying to traverse through the network on port 445.
Host-based Indicators: Identify the host-based indicators of this malware.
- Using Procmon:
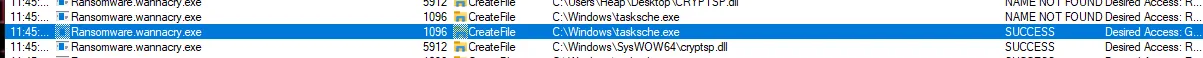
- Looking at the createFile operation one the files created is tasksche.exe.
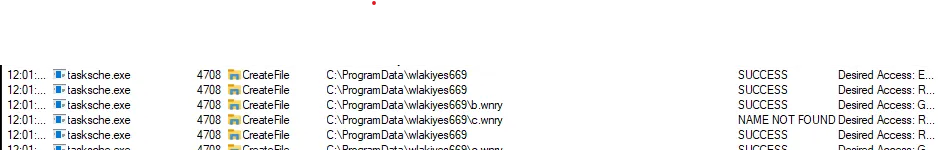
- Checking tasksche.exe process Name, wlakiyes669 created with multiple files created inside.
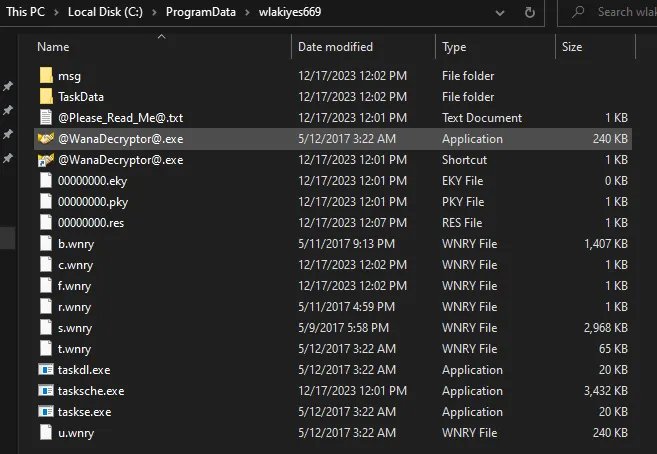
- Checking the folder multiple executebles and *.wnry located.
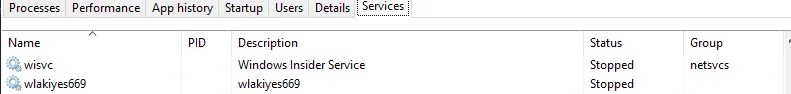
- Upon opening task manager service tab, Service creation with the exact name as the directory. This is a persistence mechanism used to encrpyt any new files added to the system and allow wannacry to launch when restarting the computer.
Use Cutter to locate the killswitch mechanism in the decompiled code and explain how it functions.
- Using Cutter:
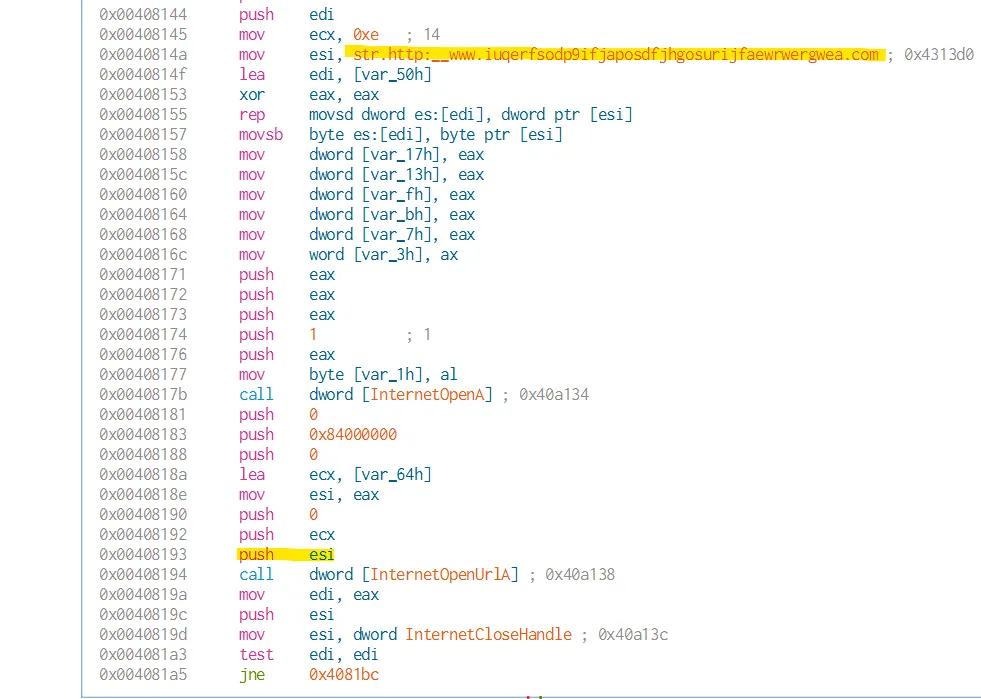
- The url is loaded to esi and esi pushed to the stack to be used when calling InternetOpenUrlA ( which will try opening the resource through HTTP URL)
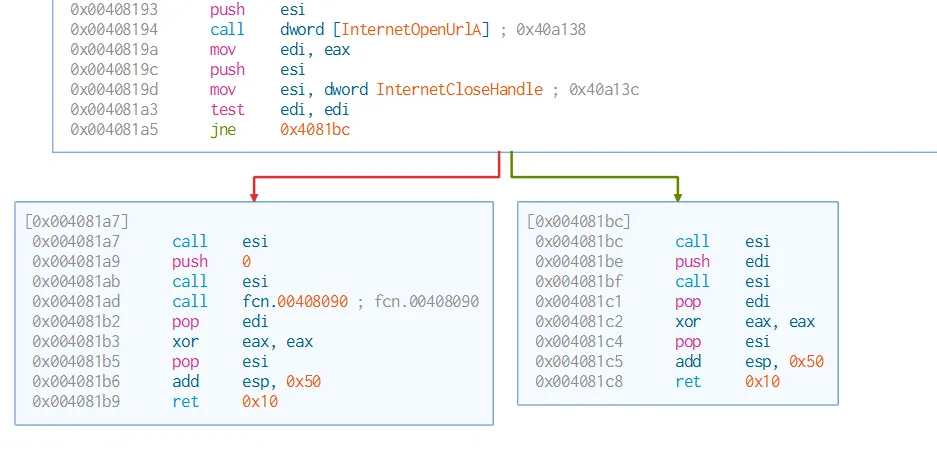
- We can see the logic of the program, so edi is the result returned from InternetOpenUrlA. test edi, edi will see if the value returned is 0 or 1.
- If the it returns 0 flag will go to the left side which is similar to the right side except with call
fcn.00408090which is responsible for the encryption of the program and the rest of the routine. - While the other side just exits the program. So, if the program is able to connect to the URL specified it won’t launch its malicious behaviour.
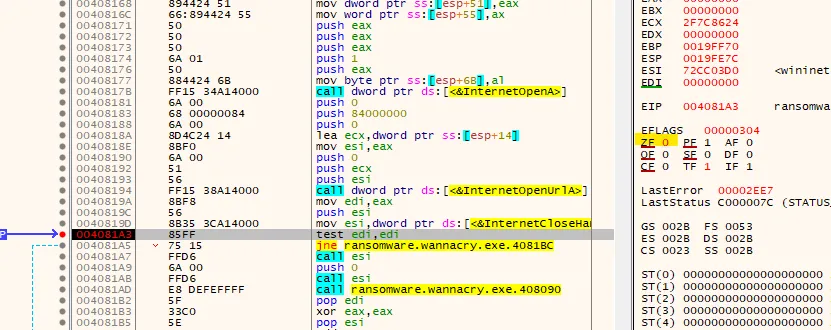
- If the it returns 0 flag will go to the left side which is similar to the right side except with call
- Using x32dbg, locating where
test edi edi, we can see flipping the ZE flag to 0 will prevent the program from executing the malicious behaviour.
